




What Is a Business Continuity Plan?
A business continuity plan proactively outlines that steps that you will take in your business to recover from (and in some cases prevent) disasters that may occur. The goal is to analyze potential threats, identify essential areas of the business that need to be focused on first, and clearly outline what should happen to avoid lost revenue or sustained business disruption.Your Business Continuity is our Priority
BCP involves defining any and all risks that can affect the company’s operations, making it an important part of the organization’s risk management strategy. Risks may include natural disasters—fire, flood, or weather-related events—and cyber attacks.SOLUTIONS
Continuity Planning & Disaster Recovery
There are several steps many companies must follow to develop a solid BCP. They include:
- Business Impact Analysis: Here, the business will identify functions and related resources that are time-sensitive.
- Recovery: In this portion, the business must identify and implement steps to recover critical business functions.
- Organization: A continuity team must be created. This team will devise a plan to manage the disruption.
- Training: The continuity team must be trained, completing exercises that go over the plan and strategies.
- Checklist: Create a list that includes key details such as emergency contact information.
Virtualization & High Availability
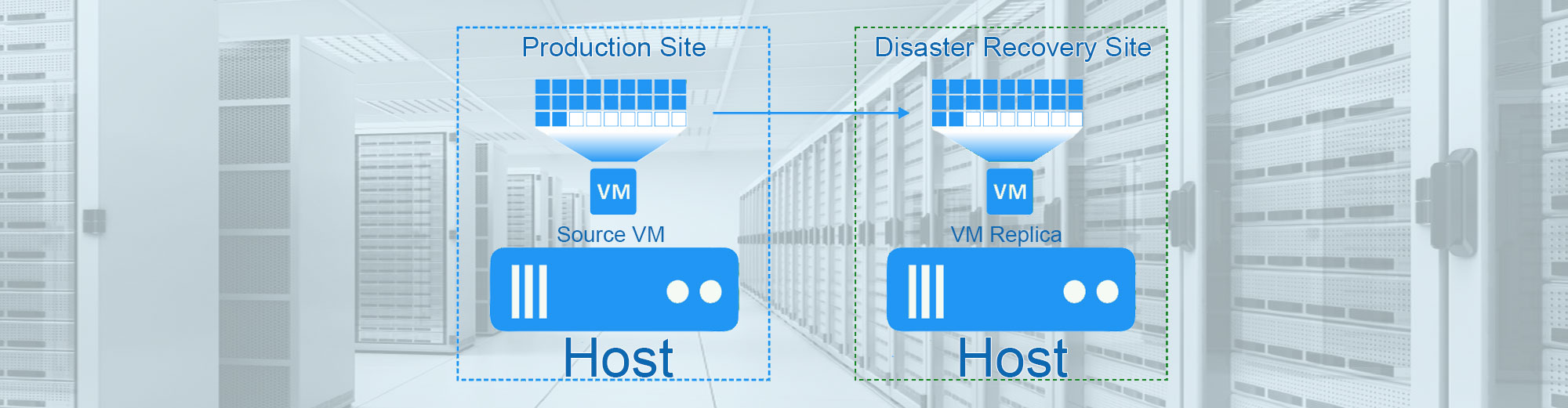
High Availability provides uniform, cost-effective fail-over protection against hardware and operating system outages within your virtualized IT environment. High Availability allows you to: Monitor VMware vSphere hosts and virtual machines to detect hardware and guest operating system failures.
Virtualization Checklist
Define the VMs to be mirrored. The members of a server cluster will likely host a variety of virtual machines (VMs), so decide which VMs need protection through mirroring across servers and which less critical VMs don’t. There’s no point in duplicating VMs if it takes only two or three minutes to recover a VM on another server.
Consider server computing resources. Each VM requires CPU, RAM, I/O and network connectivity, so assign and balance workloads to stay within the available computing power of each server. Be sure to consider the added computing requirements for duplicated — mirrored — or failed-over VMs.
Select VM mirroring software. Mirroring software must be fully interoperable with the hypervisor on each server, as well as the applications being protected. For example, everRunVM from Marathon Software can protect Exchange, SQL, SharePoint and BlackBerry services and is fully compatible with Citrix Systems Inc.’s XenServer.
Test failover/failback regularly. Once tested and deployed, it’s important to verify HA readiness by periodically testing the failover/failback behavior of mirrored VMs. The trigger may be as simple as disconnecting a network cable from one server and verifying that the mirrored VM continues application availability from the second server without disruption.
Maintain virtualization high availability in backup regimen. Protecting VMs with HA is often considered a form of DR, but even mirrored VMs need to be backed along with other nonmirrored VMs. Backups can be performed from a SAN to other storage or off-site locations using a variety of software tools.
